This is a review of the second edition of Solutions Architect’s Handbook, published by Packt and authored by Saurabh Shrivastava and Neelanjali Srivastav. The reason behind the review is that most often we Technical Program Managers (TPMs) focus primarily on System...
Understanding Recommendation Systems: Using Various Filtering Techniques
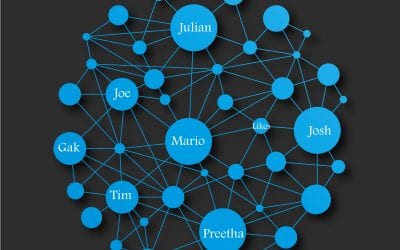
Every B2C website or app that we use today from Amazon, LinkedIn, Facebook, Netflix, Instagram uses some form of recommendation engine. In this post we will go over Understanding Recommendation Systems: Using Various Filtering Techniques and understand their...
Key Reasons Why Move To The Cloud
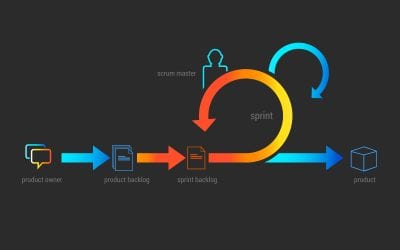
The fundamental reason to move to an Agile development model was to get new features and products to the customer's hands sooner. The goal was to add value to our customers in the fastest possible way. Five to seven years ago we saw the move towards the agile...
Building Resilient Microservices – A Guide for TPMs
As Technical Program Managers, we are often tasked with leading teams in Building Resilient Microservices. This post goes into all the things a TPM needs to keep in mind while building microservices We are going to discuss best practices for Building resilient,...
Microservices – Architecture, Advantages and Disadvantages
Microservices is the new buzz word. It refers to smaller and more manageable services that serves a specific use case. They are the exact opposite of a mololytictic application where you have a self contained application that would carry out any and all requests that...
What is Kafka – All You Need to Know About Kafka and Kafka Cluster
Kafka is a distributed, partitioned,high-throughput, low-latency platform. It provides a similar functionality of a messaging system, but with a unique design. Let us go over some basic messaging terminology related to Kafka - Kafka maintains feeds of messages in...
What is NoSQL? Why NoSQL & Types of NoSQL Database
Over the last decade there has been an explosion of users we probably had 1000 users per day hitting high-traffic websites and today we have millions of users. Millions of users mean that applications need to handle the load of multiple users accessing the same data...
A True Agile Implementation?
Are there teams you have worked in that follow a flavor of an Agile implementation be it Scrum or TTD or Kanban to the letter? And if so do you do it because you feel the need to implement a method and all its guidelines or do you do it because it is what the team...
User Experience Maturity Models
A customer's user experience cannot be understated. All successful B2C products try to ensure that the user experience is well throughout. Every webpage or app you use runs 100s of usability tests every month to ensure that they provide the customer with the best...
Content Delivery Network – How it Works and What are its Benefits
Content Delivery Network - CDN primary goal is to deliver data to the end-user with high availability and high performance. The CDN network accomplishes this by hosting the data as close to the end-user as possible. This is achieved via a geographical distribution of...
Why Infrastructure as Code (IaC) is Important
INFRASTRUCTURE AS CODE (IaC) I believe as TPMs we often are the guiding compass for our teams. We should always be looking at industry-wide trends and nudge our teams in the right direction. Having said that it is quite necessary to keep an eye out on what's happening...
Microsoft Program Manager Interview: With Alessandro Catorcini – Part II
Technical Program Manager Interview: With Alessandro Catorcini A fabulous interview with Alessandro Catorcini! He has over 20 years of experience in tech. He spent over 15 years at Microsoft in various roles from being a software architect, a Principal Group Program...
Cloud Computing for Managers – (TPM’s, PM’s, SDM’s)
Cloud Computing for Managers - (TPMs, PMs, SDMs) Over the last couple of years, there has been a need for managers (TPMs, PMs, SDMs) to have a good knowledge of the workings of the cloud. We have seen the move from a three tire service-based architecture to...
HTTP vs HTTPS – Similarities and Differences
In back to the basics for TPMs, we will go over the differences between HTTP vs HTTPS. We will understand HTTP & HTTPS independently and then dive into the need for HTTPS. After which we will move into discussing where they are similar and where HTTPS adds value....
AWS Solution Architect Certification & How I Aced it..
I recently passed the AWS Solution Architect - Associate Certification and decided to give you a quick run down of the exam process. The Amazon AWS Solution Architect Exam is currently one of the most highly sought after technical certifications in the industry and...
Networking Protocols & TCP/IP
This post is to cover some of the most basic things you need to know about Networking Protocols & TCP/IP in your daily world. Let's go over some of the very basic terms that a PGM needs to know of Protocol - This is the set of rules used for communication. Think...
Docker
Docker Containers What are docker containers? Docker is a platform for developing, shipping, running applications using container virtualization technology. Docker aids in separating your application from your infrastructure and helps in treating your Infrastructure...
Mesh Networks – The Next Big Thing?
Mesh Networks are best described as a redundant Network in which every user or node connected to the network aids in the distribution of data across the network. In other words you connect to the network via any form of message transfer protocol Bluetooth, LAN, TCP/IP...
Application Resource Utilization
More of a continuation from my previous post on Capacity Planning. The Application Resource Utilization primarily identifies the key factors that impact the response times and throughput of applications. As you tune your Application it is imperative to understand the...
IT Capacity Planning For Backend Applications
IT capacity planning for this post primarily focuses on estimating, infrastructure-related tasks that need to be considered to make sure you have enough resources to take on the projected/future traffic and computational demands for new features. A lot of sizing and...
Graph Database
What is a Graph Database ? Graph databases address one of the biggest use cases, they leverage complex dynamic relationships between data points to generate insightful correlations. Graph Databases A graph database consists of several nodes (vertices) with various...
Continuous Integration – True Agility For Software Development
Continuous delivery is the implementation of the developing, compiling, deploying, testing, and releasing software in an automated fashion with an aim to compress the time to release. Continuous delivery or continuous integration aims to have a quick and automated...
Certifications – To do or not to do
The sheer number of certifications one can do is infinite. Companies like Microsoft and Oracle alone have more than you could possibly count. From my first-hand experience, I could tell you both of these companies do not hold any value to these certifications when you...
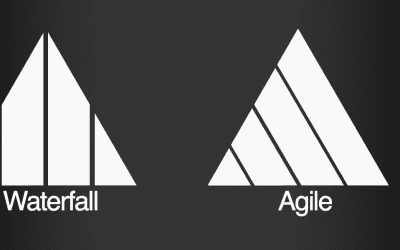
Agile vs Waterfall – The similarities !
A quick recap of the Agile Manifesto Individuals and interactions over processes and tools Working software over comprehensive documentation Customer collaboration over contract negotiation Responding to change over following a plan. That is, while there is value in...
OAuth 2 – The Fundamentals and Entities in an O-Auth Flow
What is OAuth 2.0? If you are a frequent app user using new apps you most likely have used OAuth 2. OAuth provides an application a form of Authentication and Authorization. Authentication confirms you are who you say you are, while authorization is to give a third...
Preparing For Your Upcoming TPM Interview
Subscribe